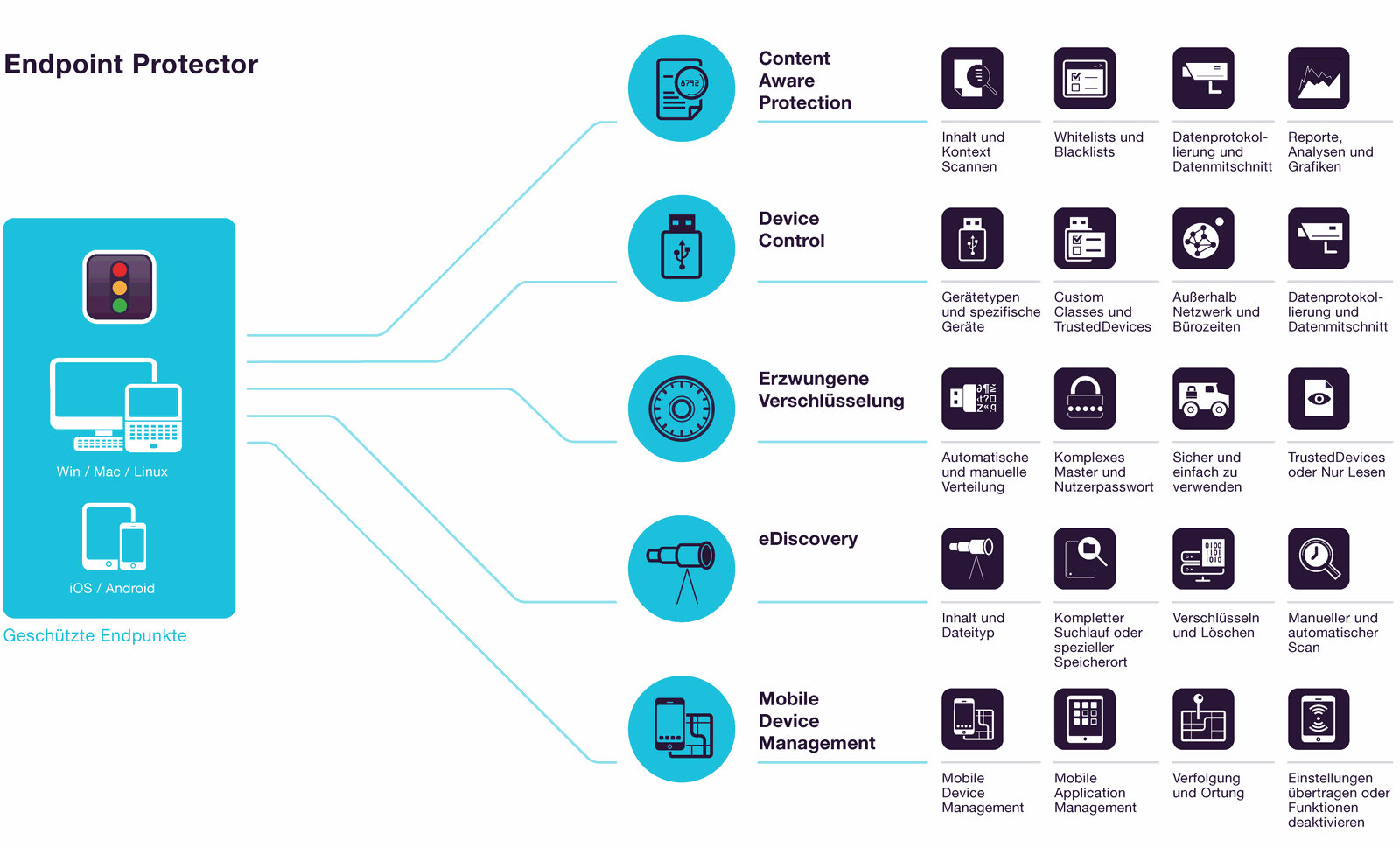
Endpoint Protector
Platform-independent data loss prevention
Award Winning Data Loss Prevention / On-Premises DLP for Corporations
as well as small and medium enterprises.
Endpoint Protector
On-premises Full DLP for corporations and mid-sized companies, available as hardware or virtual appliance as well as for cloud hosting.
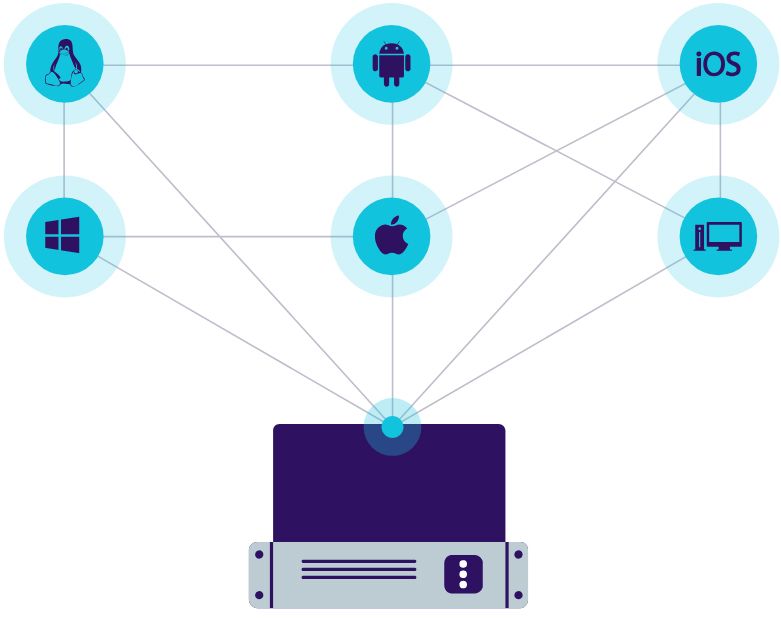
Easy-to-use, platform-independent data loss prevention tools that provide seamless protection of USB and peripheral ports, scan data transfers and data at rest, enforce encryption, and provide enterprise mobility management
- For Win / Mac / Linux
- Commissioning in 30 minutes
- Unbeatable features
- Common Criteria EAL 2 certification
Content Aware Protection (CAP) for WIN, macOS, LINUX
Scan movement data
Monitor, control and block file transfers. Detailed control through content and contextual review.
Exit Points Blacklist
Filters can be set based on a large list of monitored applications. USB storage devices, network shares and other exit points can be monitored for content.
File Type Blacklist
File Type Filters can be used to block specific documents based on their extension, even if these are manually modified by users.
Predefined Content Blacklist
Filters can be created based on predefined content such as Credit Card Numbers, Social Security Numbers and many more.
Custom Content Blacklist
Filters can also be created based on custom content such as keywords and expressions. Various Blacklist Dictionaries can be created.
File Name Blacklist
Filters based on file names can be created. They can be set based on the file name and extension, just the name or just the extension..
File Location Blacklists and Whitelists
Filters based on files' location on the local HDD. These can be defined to include or exclude containing subfolders.
Regular Expressions Blacklist
Advanced custom filters can be created to find a certain recurrence in data transferred across the protected network.
Allowed File Whitelists
While all other attempted file transfers are blocked, whitelists can be created to avoid redundancy and increase productivity.
Domain & URL Whitelisting
Erlaubt whitelistbasiert Firmenportale oder Emailadressen, damit Mitarbeiter bei der Arbeit flexibel bleiben und zugleich die Unternehmensrichtlinien umgesetzt werden können.
Print Screen and Clipboard Monitoring
Revoke screen capture capabilities. Eliminate data leaks of sensitive content through Copy & Paste / Cut & Paste, enhancing the data security policy.
Optical Character Recognition
Inspect content from photos and images, detecting confidential information from scanned documents and other similar files.
File Tracing and File Shadowing
Record all file transfers or attempts to various online applications and other exit points. Have a clear view of actions by saving a copy of the files.
Threshold for Filters
Define up to which number of violations a file transfer is allowed. It applies to each type of content or to the sum of all violations.
Transfer Limit
Contextual Content Scanning
Enable an advanced inspection mechanism for a more accurate detection of sensitive content such as PIIs. Context customization is available.
Offline Temporary Password
Temporarily allow file transfers to computers disconnected from the network. Ensure security and productivity.
Dashboards, Reports and Analysis
Monitor activity related to file transfers with a powerful reporting and analysis tool. Logs and reports can also be exported to SIEM solutions.
Compliance (DSGVO, HIPAA etc.)
Become compliant with industry rules and regulations like PCI DSS, GDPR, HIPAA etc. Avoid fines and other prejudices.
DLP for Printers
Policies for local and network printers to block printing of confidential documents and prevent data loss and data theft.
DLP for Thin Clients
Protect data on Terminal Servers and prevent data loss in Thin Client environments just like in any other type of network.
More functions / Many other functions are available. Ask us!
Device Control (DC) for WIN, macOS, LINUX
Check USB and peripheral ports
Lock, monitor and manage devices.
Granular control based on manufacturer ID, product ID, serial number and other criteria.
Set Rights Granularly
Device Rights can be configured globally, per group, computer, user and device. Use default settings or adjust as needed.
Device Types and Specific Device
Set rights - deny, allow, read only, etc. - for Device Types or Specific Devices (using VID, PID and Serial Number).
Custom Classes
Rights can be created based on classes of devices making management easier for products from the same vendor.
Outside Hours Policies
Device Control Policies can be set to apply when outside normal working hours. Business hours start & end time and working days can be set.
Outside Network Policies
Device Control Polices can be set to apply when outside the company's network. Enforcement is based on DNS Domain Names and IP Addresses.
Active Directory Sync
Take advantage of AD to make large deployments simpler. Keep entities up to date, reflecting the network groups, computers and users.
Users and Computers Information
Gain a better visibility with information such as Employee IDs, Teams, Location, accurate contact details and more (IPs, MAC Addresses, etc.)
File Tracing
Record all file transfers or attempts to various online applications and cloud services, providing a clear view of users’ actions.
File Shadowing
Save a copy of files that were transferred to controlled devices that can later be used for auditing purposes.
Offline Temporary Password
Temporarily allow file transfers to computers disconnected from the network. Ensure security and productivity.
Create E-Mail Alerts
Predefined and Custom e-mail alerts can be set up to provide information on the most important events related to device use.
Dashboard and Graphics
For a quick visual overview of the most important events and statistics, graphics and charts are available.
Report and Analysis
Monitor all activity related to device use with a powerful reporting and analysis tool. Logs and reports can also be exported.
More functions / Many other functions are available. Ask us!
Enforced Encryption (EL) for WIN, macOS
Automatic USB encryption
Verschlüsseln, verwalten und sichern Sie USB-Speichergeräte, indem Sie vertrauliche Bewegungsdaten schützen.
Passwort basiert, einfach zu bedienen und sehr effizient.USB Enforced Encryption
Authorize only encrypted USB devices and ensure all data copied on removable storage devices is automatically secured.Automatic deployment and Read Only
Both automatic and manual deployment is available. The option to allow Read Only rights until encryption is needed is also possible.Complex Master and User Passwords
The password complexity can be set as needed. The Master Password provides continuity in circumstances like users' password resets.More functions / Many other functions are available. Ask us!
eDiscovery (ED) for WIN, macOS, LINUX
Scan idle data
Detect, encrypt and delete sensitive data. Detailed content and context inspection through manual or automatic scans.
Encrypt and Decrypt Data
Data at rest containing confidential information can be encrypted to prevent unauthorized employees’ access. Decryption actions are also available.Delete Data
If clear violations of the internal policy occur, delete sensitive information as soon as it is detected on unauthorized endpoints.Scan Location Blacklist
Filters can be created based on predefined locations. Avoid redundant scanning for data at rest with targeted content inspections.Automatic Scans
In addition to the Clean and Incremental Scans, Automatic Scans can be scheduled – either one time or recurring (weekly or monthly).File Tracing
Record all file transfers or attempts to various online applications and cloud services, providing a clear view of users’ actions.Reports and Analysis
Monitor logs relating to scanning data at rest and take remediation actions as needed. Logs and reports can also be exported to SIEM solutions.Threshold for Filters
Define up to which number of violations a file transfer is allowed. It applies to each type of content or to the sum of all violations.Compliance (DSGVO, HIPAA etc.)
Become compliant with industry rules and regulations like PCI DSS, GDPR, HIPAA etc. Avoid fines and other prejudices.SIEM Integration
Leverage Security Information and Event Management products by externalizing logs. Ensure a seamless experience across security products.File Type Blacklist
File Type Filters can be used to block specific documents based on their extension, even if these are manually modified by users.Predefined Content Blacklist
Filters can be created based on predefined content such as Credit Card Numbers, Social Security Numbers and many more.Custom Content Blacklist
Filters can also be created based on custom content such as keywords and expressions. Various Blacklist Dictionaries can be created.File Name Blacklist
Filters based on file names can be created. They can be set based on the file name and extension, just the name or just the extension.File Location Blacklist and Whitelist
Filters based on files' location on the local HDD. These can be defined to include or exclude containing subfolders.Regular Expressions Blacklist
Advanced custom filters can be created to find a certain recurrence in data transferred across the protected network.Allowed File Whitelists
While all other attempted file transfers are blocked, whitelists can be created to avoid redundancy and increase productivity.Domain & URL Whitelisting
Enforce company policy but allow employees the flexibility they need to do their work. Whitelist company portals or email addresses.MIME Type Whitelist
Avoid redundant scanning at a global level by excluding content inspection for certain MIME Types.More functions / Many other functions are available. Ask us!
Mobile Device Management (MD) for Android, IOS, macOS
Enterprise Mobility Management
Secure, locate and manage mobile devices. Push apps and network settings or delete data remotely.
Over-the-air Enrollment for iOS & Android
The app can be brought to the device remotely via SMS, email, URL link or QR code. Choose the most convenient way for your network.Bulk Enrollment
For an efficient deployment process, up to 500 smartphones and tablets can be enrolled at the same time.Remote Lock
Remotely enable instant locking of mobile devices in case of any related incidents. Avoid data leaks due to lost or misplaced devices.Track & Locate
Closely monitor company’s mobile devices and know at all times where your company sensitive data is.Disable built-in functionalities
Control the permissions for built-in features such as camera, avoiding data breaches and loss of sensitive data.Play Sound to locate lost devices
Locate a misplaced mobile device by remotely activating a loud ringtone until it is found (only supported for Android).Mobile Application Management
Manage apps accordingly to the organization’s security policies. Instantly push free and paid apps to enrolled mobile devices.Push Network Settings
Push network settings like E-mail, Wi-Fi and VPN settings or disable them, including Bluetooth, set ringer mode, etc.Alerts
Extended Predefined System Alerts are available, as well as the option to set up Custom System Alerts.Reports and Analysis
Monitor all users’ activity related to device use with a powerful reporting and analysis tool. Logs and reports can also be exported.Kiosk Mode with Samsung Knox
Lock or contain the mobile device into specific apps. Remotely enforce security on the mobile fleet and turn them into dedicated devices.macOS Management
To extend the DLP features, Macs can also be enrolled into the MDM module, taking advan- tage of additional management options.Password Enforcement
Proactive protection of company critical data stored on mobile devices by enforcing strong password policies.Remote Wipe
For critical situations where the only way to avoid data leaks is wiping the device, this can easily be done remotely.Geofencing
Define a virtual perimeter on a geographic area, gaining a better control of the MDM policies that apply only in a specific area.iOS Restrictions
Make sure only business related use is possible. If not compliant to company policy, disable iCloud, Safari, App Store, etc.Push vCards on Android
Add and push contacts for Android mobile devices, making sure your mobile workforce can quickly get in touch with the right people.App Monitoring
Know what apps your employees are download- ing on their mobile devices, keeping a discreet line between work and leisure.Asset Management
Gain insight into the mobile device fleet about Device Names, Types, Models, Capacity, OS Versions, Carriers, IMEIs, MACs, etc.Create E-mail Alerts
Email alerts can be set up to provide information on the most important events related to mobile devices’ use.Dashboard and Graphics
For a quick visual overview of the most important events and statistics, graphics and charts are available.More functions / Many other functions are available. Ask us!
The following USER manuals are available from us on request:
-
Endpoint Protector - User Manual
-
Virtual and Hardware Appliance Deployment - User Manual
-
Cloud Services (AWS, Azure, GCP) Deployment - User Manual
-
Active Directory Deployment Guide - User Manual
-
JAMF Deployment Guide - User Manual
-
Mobile Device Management - User Manual
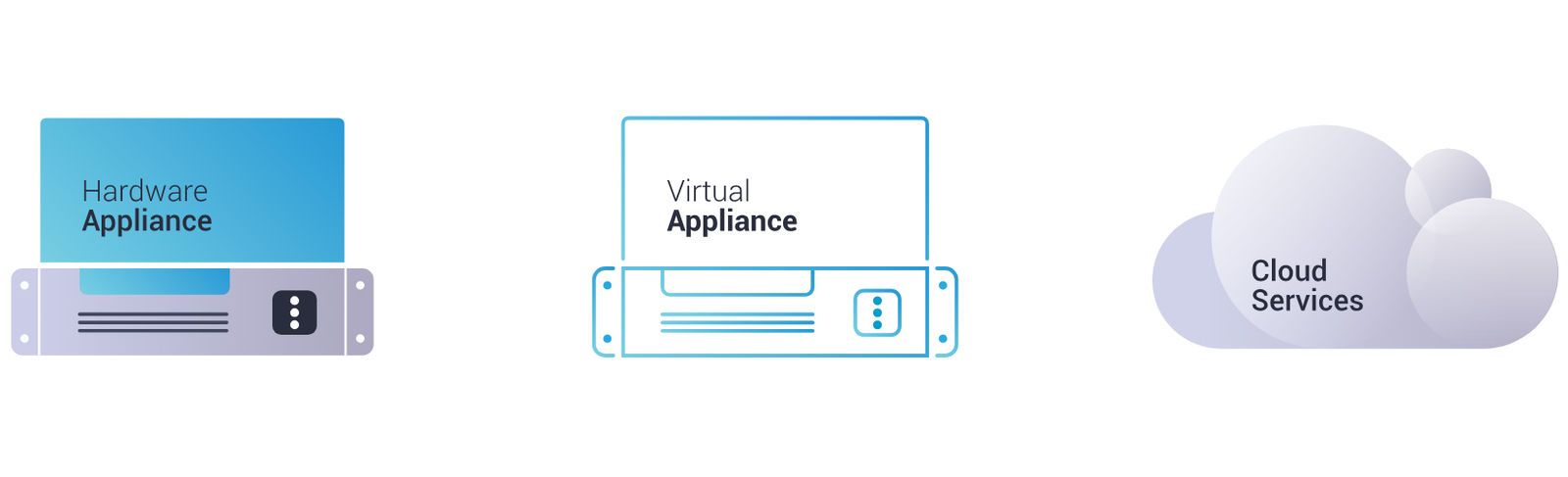
Available as hardware or virtual appliance as well as cloud service
Endpoint Protector can be deployed as a virtual or hardware-based appliance, providing fast deployment and deployment.
Layout and function
CLOSED
Wir haben unsere IT-Aktivitäten eingestellt.
Bitte wenden Sie sich direkt an unsere Produkte-Lieferanten:
Unsere Dienstleistungen finden Sie ausschliessliche in der Gesundheitsbranche wieder.